Current Focus of Research
[Research Project 5] Advanced Testing for System-on-Chip (SoC) Verification, Validation, and Assurance
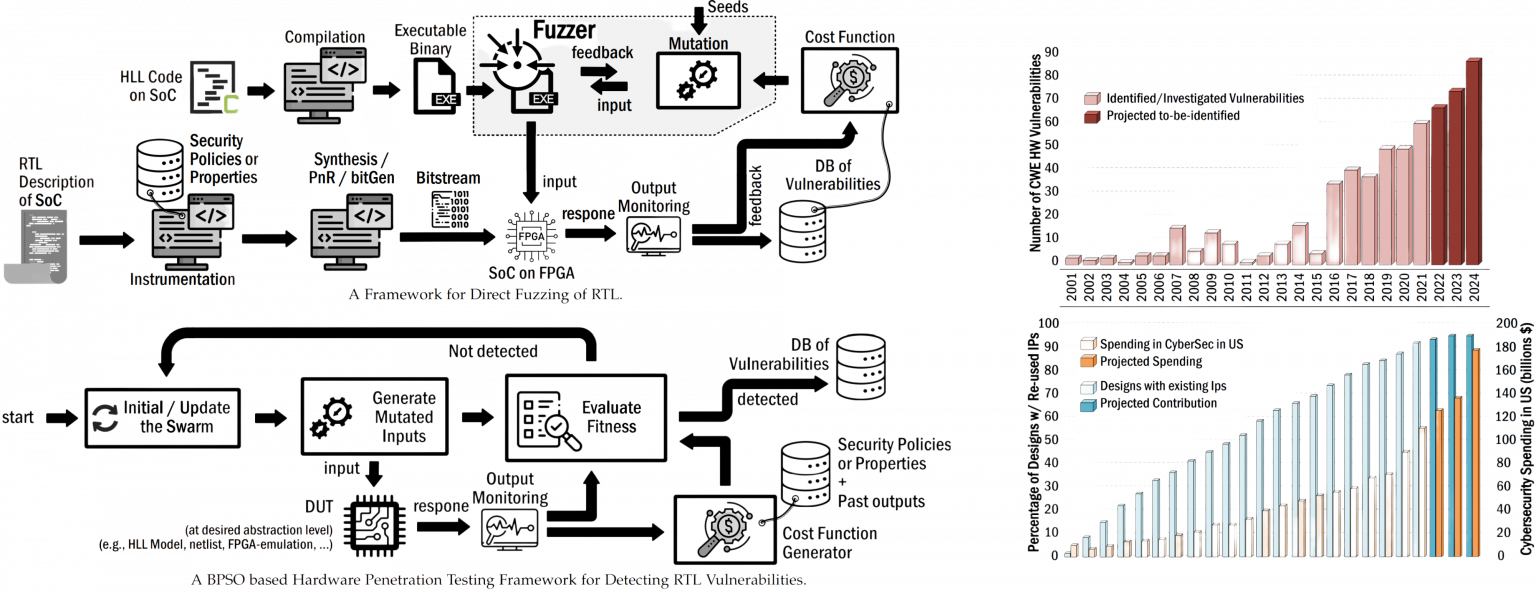
Modern System-on-Chip (SoC) architectures with numerous components and highly sensitive assets, where each may be provided by a different vendor, either trusted or untrusted, require detailed verification, validation, and assurance (protection from unauthorized access). Given the sheer size of today’s SoCs, verifying/guaranteeing the functionality and particularly security of these assets against any attacks becomes quite challenging, as existing IP-level security countermeasures have nothing to do with such SoC-level vulnerabilities and they originate mostly from out-of-spec interactions between layers/components within the SoCs. This project mainly investigates building formal definitions for threat scenarios in SoC architectures, defining security rules and properties, and security-oriented design rule checking (DRC). Throughout this project, innovative strategies to enhance the testability for security purposes have been developed, which mostly rely on advanced testing techniques, e.g., fuzz/penetration/AI testing (widely used in software), and show the potential to be implemented for detecting hardware vulnerabilities.
Selected Publications
- MM Hossain, KZ Azar, F Rahman, F Farahmandi, M Tehranipoor, “Fuzzing for Automated SoC Security Verification: Challenges and Solution,” in IEEE Design & Test, pp. 1-6, 2024.
Available online: https://ieeexplore.ieee.org/abstract/document/10471551 - NF Dipu, MM Hossain, KZ Azar, F Farahmandi, M Tehranipoor, “FormalFuzzer: Formal Verification Assisted Fuzz Testing for SoC Vulnerability Detection,” in 2024 29th Asia and South Pacific Design Automation Conference (ASP-DAC), pp. 355-361, 2024.
Available online: https://ieeexplore.ieee.org/abstract/document/10473911 - MM Hossain, A Vafaei, KZ Azar, F Rahman, F Farahmandi, M Tehranipoor, “SoCFuzzer: SoC Vulnerability Detection using Cost Function enabled Fuzz Testing,” in 2023 Design, Automation & Test in Europe Conference & Exhibition (DATE), pp. 1-6, 2023.
Available online: https://ieeexplore.ieee.org/abstract/document/10137024/ - H Al-Shaikh, A Vafaei, MMM Rahman, KZ Azar, F Rahman, F Farahmandi, M Tehranipoor, “Sharpen: SoC Security Verification by Hardware Penetration Test,” in Proceedings of the 28th Asia and South Pacific Design Automation Conference (ASP-DAC), pp. 1-6, 2023.
Available online: https://dl.acm.org/doi/abs/10.1145/3566097.3567918 - MM Hossain, NF Dipu, KZ Azar, F Rahman, F Farahmandi, M Tehranipoor, “TaintFuzzer: SoC Security Verification using Taint Inference-enabled Fuzzing,” in 2023 IEEE/ACM International Conference on Computer Aided Design (ICCAD), pp. 1-9, 2023.
Available Online: https://ieeexplore.ieee.org/abstract/document/10323726 - KZ Azar, MM Hossain, A Vafaei, H Al Shaikh, NN Mondol, F Rahman, F Farahmandi, M Tehranipoor, “Fuzz, Penetration, and AI Testing for SoC Security Verification: Challenges and Solutions,” in Cryptology ePrint Archive, 2022.
Available online: https://eprint.iacr.org/2022/394
Projects’ Sponsors


[Research Project 4] Sustainable and Reconfigurable SoC Monitoring for Zero-day Incidents
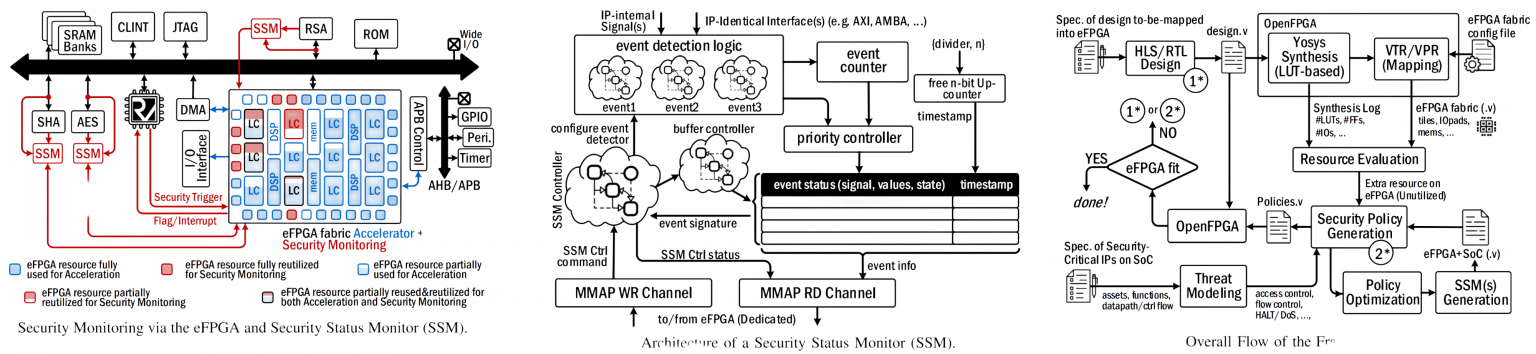
Hardware attacks threaten the integrity, confidentiality, and availability of modern SoC designs, and the number of such attacks has increased significantly. The attacks leverage the underlying vulnerabilities of SoCs, such as information and side-channel leakage, susceptibility to fault-injection attacks, malicious functionality, or even system-level vulnerabilities to exploit the critical security information of the SoCs. Many of these vulnerabilities could not be identified during design verification due to the lack of security understanding in addition to diverse threat models, large attack surfaces, high design complexity, and aggressive time-to-market. As countermeasures like system enclaves, security engines, hypervisors, etc. only offer static monitoring for SoCs’ assets (e.g., encryption/decryption keys, TRNG, configuration bits, etc.), proven inefficient for specifically emerging and zero-day attacks, this project plans to develop an upgradable security property checking mechanism, which provides the capability of adding monitoring to complex and heterogeneous SoCs. This project utilizes custom embedded field-programmable gate array (eFPGA) fabric(s) integrated into the SoC to develop a set of security policies and monitor the related activities to build a monitoring system against emerging attacks, particularly when the system is in the field. This project investigates how eFPGA can be used to add newer and updated monitoring capabilities to the targeted system, in a way that regardless of the complexity/size of the system under investigation, the proposed mechanism could be engaged with no scalability issue. Moreover, the reconfigurability of the eFPGA enhances the capability of the proposed mechanism using even more advanced techniques, such as implementing a tiny machine learning (ML) in the eFPGA fabric to help monitor specific security policies in real-time, helping to offer monitoring against different vulnerabilities, such as Ransomware, Spectre, Meltdown, Rowhammer, as well as illegal transactions such as memory protection violations, zero-day attacks, etc.
Selected Publications
- MMM Rahman, S Tarek, KZ Azar, M Tehranipoor, F Farahmandi, “The Road Not Taken: eFPGA Accelerators Utilized for SoC Security Auditing,” in IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, pp. 1-14, 2024.
Available online: https://ieeexplore.ieee.org/abstract/document/10496439 - MMM Rahman, S Tarek, KZ Azar, M Tehranipoor, F Farahmandi, “Efficient SoC Security Monitoring: Quality Attributes and Potential Solutions,” in IEEE Design & Test, pp. 1-6, 2023.
Available online: https://ieeexplore.ieee.org/abstract/document/10172244 - MMM Rahman, S Tarek, KZ Azar, F Farahmandi, “EnSAFe: Enabling Sustainable SoC Security Auditing using eFPGA-based Accelerators,” in IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), pp. 1-6, 2023.
Available online: https://ieeexplore.ieee.org/abstract/document/10313548
Projects’ Sponsors


[Research Project 3] Enabling Security in Heterogeneous Integration: Chiplet-to-SiP Integration Security
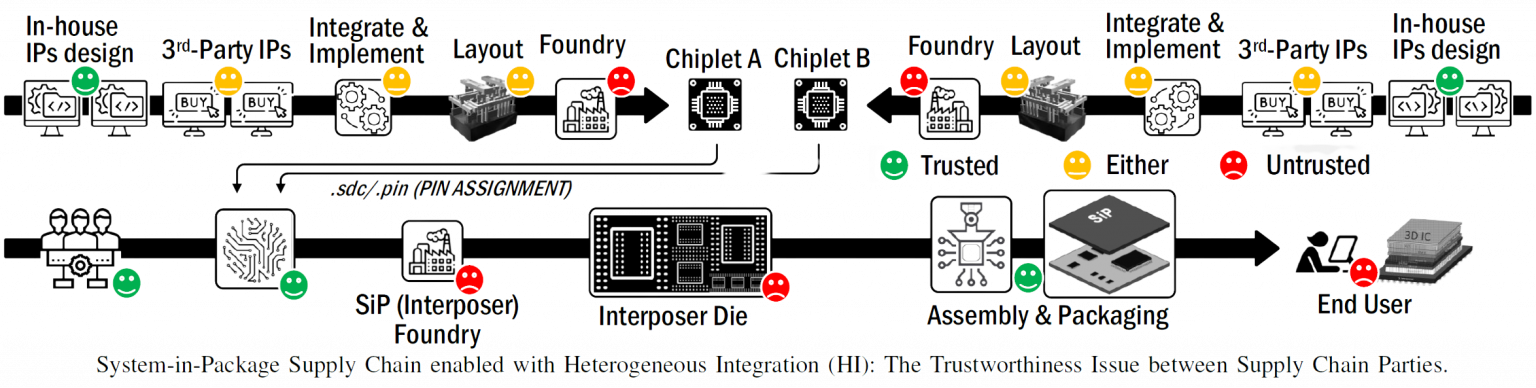
Witnessing significant signs of a slowdown of Moore’s law (as well as incentives of CHIPS act) has pushed semiconductors toward advanced packaging with heterogeneous integration (HI) to stay away from the challenges of monolithic ICs in more shrunk technology. HI involves integrating multiple silicon dies, i.e., chiplets, within a single system-in-package (SiP), connecting them onto silicon interposer layers, embedded multi-die interconnect bridges, etc. Although HI sounds more advantageous than monolithic architecture, the introduction and involvement of a growing number of parties/entities in the semiconductor supply chain, and the horizontal business model, create security challenges regarding the confidentiality, integrity, and availability (CIA) of SiPs. Taking all the threats and vulnerabilities into account in HI, this project focuses on investigating multiple avenues for building security measures in the domain of SiP, including but not limited to (i) trust validation of chiplets for SiP security, (ii) establishing secure die-to-die interface for interposer security, (iii) and introducing chiplet-level hardware security module, i.e., chiplet HSM (CHSM), for establishing trusted execution in the SiP.
Selected Publications
- MSUI Sami, T Zhang, AM Shuvo, MSU Haque, PE Calzada, KZ Azar, HM Kamali, F Rahman, F Farahmandi, M Tehranipoor, “Advancing Trustworthiness in System-in-Package: A Novel Root-of-Trust Hardware Security Module for Heterogeneous Integration,” in IEEE Access, pp. 1-27, 2024.
Available online: https://ieeexplore.ieee.org/abstract/document/10466542 - PE Calzada, MSUI Sami, KZ Azar, F Rahman, F Farahmandi, M. Tehranipoor, “Heterogeneous integration supply chain integrity through blockchain and CHSM,” in ACM Transactions on Design Automation of Electronic Systems, pp. 1-25, 2023.
Available online: https://dl.acm.org/doi/abs/10.1145/3625823 - T Zhang, ML Rahman, HM Kamali, KZ Azar, F Farahmandi, “SiPGuard: Run-time system-in-package security monitoring via power noise variation,” in IEEE Transactions on Very Large Scale Integration (VLSI) Systems, pp. 1-14, 2023.
Available online: https://ieeexplore.ieee.org/abstract/document/10286457 - T Zhang, ML Rahman, HM Kamali, KZ Azar, M Tehranipoor, F. Farahmandi, “FISHI: Fault injection detection in secure heterogeneous integration via power noise variation,” in IEEE 73rd Electronic Components and Technology Conference (ECTC), pp. 1-8, 2023.
Projects’ Sponsors

[Research Project 2] Security Evaluation of IP Protection (against IP Piracy and IC Overproduction)
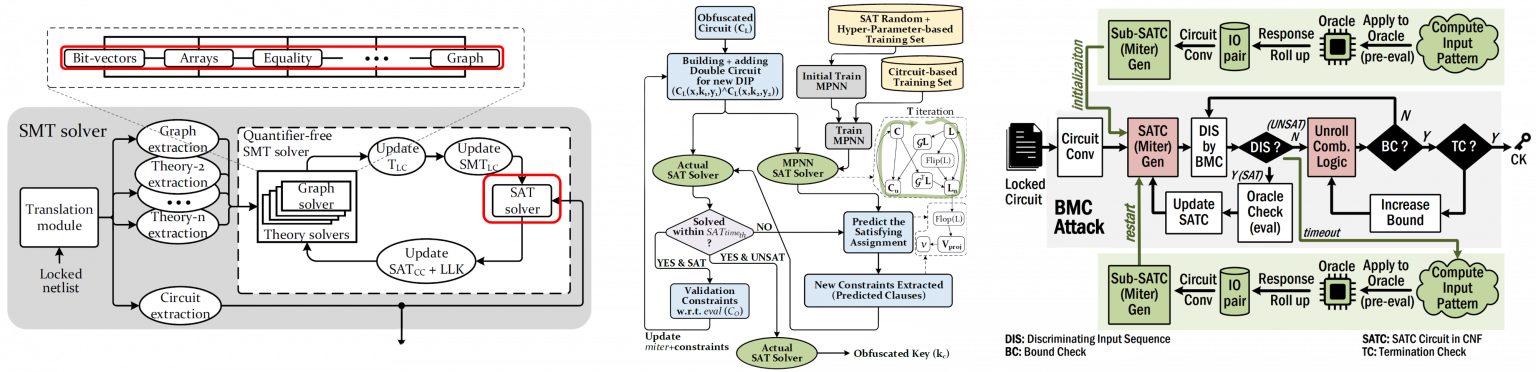
Hardware obfuscation is a technique used to protect ICs from reverse engineering, piracy, and tampering. Over the years, the security of hardware obfuscation has evolved to keep pace with the growing sophistication of attackers. In this project, with red-teaming, I developed novel attacks utilizing learning approaches (e.g., message-passing neural network model), and advanced formal and satisfiability cores (e.g., non-Boolean satisfiability modulo theory) to demonstrate the vulnerability in the state-of-the-art hardware obfuscation solutions. Funded by DoD, these approaches led to the introduction of two major research directions in security evaluation of logic locking, now known as machine learning (ML) based and non-Boolean-oriented attacks on logic locking, where more than dozens of attacks emerged derived from this project.
Selected Publications
- KZ Azar, HM Kamali, F Farahmandi, M Tehranipoor, “Improving Bounded Model Checkers Scalability for Circuit De-obfuscation: An Exploration,” in IEEE Transactions on Information Forensics and Security, pp. 2771-2785, 2024.
Available online: https://ieeexplore.ieee.org/abstract/document/10412845 - MS Rahman, KZ Azar, F Farahmandi, HM Kamali, “Metrics-to-methods: Decisive reverse engineering metrics for resilient logic locking,” in Proceedings of the Great Lakes Symposium on VLSI, pp. 685-690, 2023.
Available online: https://dl.acm.org/doi/abs/10.1145/3583781.3590273 - HM Kamali, KZ Azar, F Farahmandi, M Tehranipoor, “SheLL: Shrinking eFPGA fabrics for logic locking,” in Design, Automation & Test in Europe Conference & Exhibition (DATE), pp. 1-6, 2023.
Available online: https://ieeexplore.ieee.org/abstract/document/10137211 - KZ Azar, HM Kamali, F Farahmandi, M Tehranipoor, “Warm up before circuit de-obfuscation? An exploration through bounded-model-checkers,” in IEEE International Symposium on Hardware Oriented Security and Trust (HOST), pp. 1-4, 2022.
- HM Kamali, KZ Azar, F Farahmandi, M Tehranipoor, “Advances in logic locking: Past, present, and prospects,” in Cryptology ePrint Archive, 2022.
Available online: https://eprint.iacr.org/2022/260 - KZ Azar, HM Kamali, S Roshanisefat, H Homayoun, CP Sotiriou, A Sasan, “Data Flow Obfuscation: A New Paradigm for Obfuscating Circuits,” in IEEE Transactions on Very Large Scale Integration (VLSI) Systems, pp. 1-14, 2021.
Available online: https://ieeexplore.ieee.org/abstract/document/9369866 - KZ Azar, HM Kamali, H Homayoun, A Sasan, “NNgSAT: Neural network guided SAT attack on logic locked complex structures,” in Proceedings of the 39th International Conference on Computer-Aided Design (ICCAD), pp.1-9, 2020.
Available online: https://dl.acm.org/doi/abs/10.1145/3400302.3415669 - S Roshanisefat, HM Kamali, KZ Azar, SMP Dinakarrao, N Karimi, H Homayoun, A Sasan, “DFSSD: Deep faults and shallow state duality, a provably strong obfuscation solution for circuits with restricted access to scan chain,” in 2020 IEEE 38th VLSI Test Symposium (VTS), pp. 1-6, 2020.
Available online: https://ieeexplore.ieee.org/abstract/document/9107629 - KZ Azar, HM Kamali, H Homayoun, A Sasan, “SMT attack: Next generation attack on obfuscated circuits with capabilities and performance beyond the SAT attacks,” in IACR Transactions on Cryptographic Hardware and Embedded Systems, pp. 97-122, 2019.
Available online: https://tches.iacr.org/index.php/TCHES/article/view/7335
Projects’ Sponsors




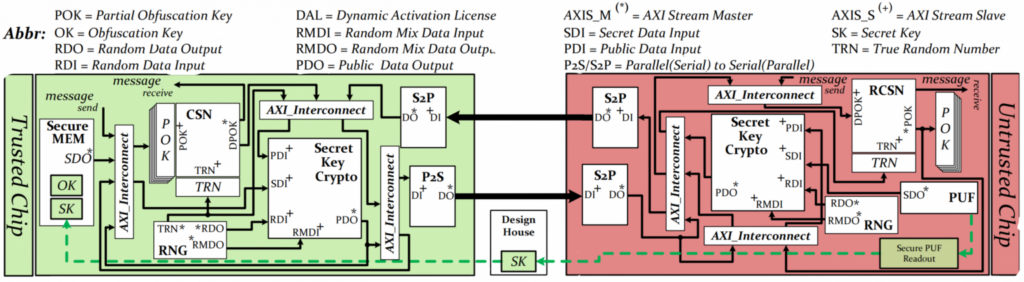
[Research Project 1] Forward Trust in IC Supply Chain
Although hardware obfuscation brings in the notion of adding protection to IP/IC against the untrusted parties throughout the IC supply chain, integrating such a mechanism alone into the ICs and leaving the supply chain intact would not be enough to be against such threats. This project aimed to investigate how an end-to-end trust could be established in the IC supply chain while security activation (e.g., obfuscation activation) is in place. This includes secure design for testability (i.e., scan chain protection in IC design and testing), enabling forward implication for secure testing, secure communication via primitives for remote activation (advantageous especially in 3D design and IoT applications), and enabling uniqueness for activation. Such solutions significantly limit the advantages gained by the adversary for different attacks. With numerous applications, this project is of great interest to the IC supply chain community.
Selected Publications
- HM Kamali, KZ Azar, S Roshanisefat, A Vakil, A Sasan, “Extru: A lightweight, fast, and secure expirable trust for the internet of things,” in 2020 IEEE 14th Dallas Circuits and Systems Conference (DCAS), pp. 1-6, 2020.
Available online: https://ieeexplore.ieee.org/abstract/document/9330632 - KZ Azar, F Farahmand, HM Kamali, S Roshanisefat, H Homayoun, W Diehl, K Gaj, A Sasan, “{COMA}: Communication and Obfuscation Management Architecture,” in I22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID), pp. 181-195, 2019.
Available online: https://www.usenix.org/conference/raid2019/presentation/azar - HM Kamali, KZ Azar, H Homayoun, A Sasan, “Full-lock: Hard distributions of sat instances for obfuscating circuits using fully configurable logic and routing blocks,” in Proceedings of the 56th Annual Design Automation Conference (DAC), pp. 1-6, 2019.
Available online: https://dl.acm.org/doi/abs/10.1145/3316781.3317831
Projects’ Sponsors


